My electron life
Monday, 18 May 2015
Hacking Metaspoitable2 without Metaspoit
So been in my new job now for some time and still have not taken my Cisco courses but never mind there is nothing like procrastinating.
So Metaspoitable2 is a vulnerable by design VM that hosts numerous miss-configured" services that will allow exploitation. I downloaded my copy from sourceforge.
For the running the VM I used the latest version of VMware Player, you need to extract the files from the compressed folder, but if you are reading this that should not be a problem for you.
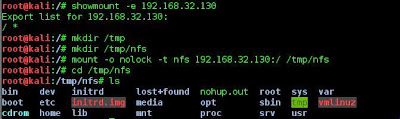
Right so first things first lets start with a basic nmap scan.
As you can see there are many ports running services on Metaspoitable2.
The service I am interested in is nfs running on port 2049.
Now nfs is a network file system or a network share.
So the next plan is to check to see were in the file system the share is located and then attempt to mount it.
The showmount command gives an output of / * meaning that the root of the directory is shared. I then mounted the nfs into /tmp/nfs now we have control of the file system.
Now this took a little time to get to and now you need to looking at how the system works.
Referring back to the nmap we can see that ssh is enabled.
Now as we have access to the file system it is possible to generate an ssh key and add it to the authorized keys file.
This will allow you to ssh in to Metaspoitable2 as root without having to provide a password, going by the rules of 2 is 1, 1 is none we currently have nothing.
The reason we have nothing is because if a server admin were to update the authorize_keys file then we would loose access. So to ensure access why don't we extract the user passwords for the server.
So as the passwords are encrypted we need to unshadow the passwd and shadow files. The output is then feed into John the Ripper giving 6 usernames and passwords within 2 seconds but not the root password, I left mine running for quite some time and never got the password, however if you ssh in as msfadmin you can use the command sudo su to elevate to root.
Labels:
hacking,
IT,
John the Ripper,
Kali,
Kali Linux,
metaspoilt,
metaspoitable,
metaspoitable2,
nfs,
nmap,
root,
ssh,
sudo
Friday, 3 October 2014
Capturing a WPA handshake.
So latest up date I had an interview about a week ago, walked out of there feeling great. Looks like it payed off, was offered the job and am just finalising the contracts now.
Lets get on to something more interesting than my boring life.
Without getting in to too much WiFi theory to get on to a WPA2 WiFi network the fist step is to capture the WPA handshake.
This is a 4 way handshake between the AP and device that initiates the connection. Basically the AP and device confirming what the pre-shared key is.
I am not trying to teach WiFi theory or anything like that just pass on my process for capturing handshakes, as always you should only be doing this to equipment you own or have permission to audit.
Now you have to start with a WiFi radio that supports packet injection and monitor mode. Offensive Security has a list of suggested hardware here for their WiFu course. Now aircrack-ng is available no windows but I prefer to use Kali Linux.
Now first thing to do is to bring up a monitor interface and personally set a custom MAC address and disable the wlan0 device.
The next step is to run airodump-ng I normally run this twice the first time for reconnaissance, to get my target ESSID , BSSID and channel.
My attack run I use this command:
"airodump-ng --bssid 20:2B:C1:6B:D8:C5 -c 11 -w BTHub3-3M6H --output-format pcap mon0"
Now lets just break this down a little.
--bssid filters by the bssid of the desired AP
-c locks mon0 on to the desired channel
-w names the capture file the out put would be "/root/BTHub3-3M6H-01.cap"the id number at the end will increment.
--output-format sets the desired format of the output file.
Once this has been run you will get an updating output.
Now as you can see we have detected the AP and a client, in this case my iPhone. In order to capture the WPA handshake we need to de-authenticate the client from the AP.
One thing to be careful of at this stage is flooding with deauth's ( -0 attribute ) this exposes the attack as you are actually transmitting, using my method you are only sending 1 deauth so you may need to rerun this command to capture the WPA handshake.
You have now captured a WPA handshake and can go on to break it using a variety of methods.
Here is my You Tube video to go along with this post.
Now here is a list of every command used - items inside {} are variables that you need to set.
airmon-ng start {wifi interface}
ifconfig {wifi interface} down
ifconfig {monitor interface} down
macchanger -m{desired MAC address} {monitor interface}
ifconfig {monitor interface} up
airodump-ng {monitor interface}
airodump-ng --bssid {bssid} -c {channel} -w {title} --output-format pcap {monitor interface}
airepaly-ng -0 1 -a {bssid} -c {client MAC} {monitor interface}
Lets get on to something more interesting than my boring life.
Without getting in to too much WiFi theory to get on to a WPA2 WiFi network the fist step is to capture the WPA handshake.
This is a 4 way handshake between the AP and device that initiates the connection. Basically the AP and device confirming what the pre-shared key is.
I am not trying to teach WiFi theory or anything like that just pass on my process for capturing handshakes, as always you should only be doing this to equipment you own or have permission to audit.
Now you have to start with a WiFi radio that supports packet injection and monitor mode. Offensive Security has a list of suggested hardware here for their WiFu course. Now aircrack-ng is available no windows but I prefer to use Kali Linux.
Now first thing to do is to bring up a monitor interface and personally set a custom MAC address and disable the wlan0 device.
The next step is to run airodump-ng I normally run this twice the first time for reconnaissance, to get my target ESSID , BSSID and channel.
My attack run I use this command:
"airodump-ng --bssid 20:2B:C1:6B:D8:C5 -c 11 -w BTHub3-3M6H --output-format pcap mon0"
Now lets just break this down a little.
--bssid filters by the bssid of the desired AP
-c locks mon0 on to the desired channel
-w names the capture file the out put would be "/root/BTHub3-3M6H-01.cap"the id number at the end will increment.
--output-format sets the desired format of the output file.
Once this has been run you will get an updating output.
Now as you can see we have detected the AP and a client, in this case my iPhone. In order to capture the WPA handshake we need to de-authenticate the client from the AP.
One thing to be careful of at this stage is flooding with deauth's ( -0 attribute ) this exposes the attack as you are actually transmitting, using my method you are only sending 1 deauth so you may need to rerun this command to capture the WPA handshake.
You have now captured a WPA handshake and can go on to break it using a variety of methods.
Here is my You Tube video to go along with this post.
Now here is a list of every command used - items inside {} are variables that you need to set.
airmon-ng start {wifi interface}
ifconfig {wifi interface} down
ifconfig {monitor interface} down
macchanger -m{desired MAC address} {monitor interface}
ifconfig {monitor interface} up
airodump-ng {monitor interface}
airodump-ng --bssid {bssid} -c {channel} -w {title} --output-format pcap {monitor interface}
airepaly-ng -0 1 -a {bssid} -c {client MAC} {monitor interface}
Tuesday, 16 September 2014
Looks like I have been silent.
_1481_1480.png) Well hi looks like I have been neglecting my blog.
Well in the last few months I have been given notice on my current contract, I have a few weeks left working at my current site and don't yet have a replacement. Good job that I have some savings, I could take a long holiday and I would end up maybe making a few more posts but is anyone even reading this?
Well hi looks like I have been neglecting my blog.
Well in the last few months I have been given notice on my current contract, I have a few weeks left working at my current site and don't yet have a replacement. Good job that I have some savings, I could take a long holiday and I would end up maybe making a few more posts but is anyone even reading this?So what have I been doing mostly studying for my MCSA on Server 2012, and guess what I have passed. I'm now looking for infrastructure jobs so here is hoping I can get a nice job in London.
I really do need to get my shit together a new WiFi Pineapple firmware was released at DEFCON, witch I once again missed really hoping to make the trip to Vegas next year. Its now 03:14 and I'm hoping to get something on here at the weekend, I'm currently studying for CCENT so I am hoping that I will be able to do something along the network side of life.
Wednesday, 16 April 2014
Pineapple Firmware 1.3.0 Salmonosaurus & Evil Portal
Salmonosaurus
Well the good people of Hak5 have gone and released another update for the Wi-Fi Pineapple.so lets start with the details of the changelog.
Changelog:
Merged upstream changes
Updated wireless drivers.
Updated wireless utilities.
Updated OpenSSL (fixed heartbleed).
Updated some other base components.
Updated hostapd.as
More stable AP.
More stable clientmode.
Faster response times.
Cleaner, more concise log output.
Timestamps added to log
Much faster webinterface view of log
Added proper vFat support
Updated all system infusions to their latest versions
Security fixes
Other minor fixes and improvements.
Updated wireless drivers.
Updated wireless utilities.
Updated OpenSSL (fixed heartbleed).
Updated some other base components.
Updated hostapd.as
More stable AP.
More stable clientmode.
Faster response times.
Cleaner, more concise log output.
Timestamps added to log
Much faster webinterface view of log
Added proper vFat support
Updated all system infusions to their latest versions
Security fixes
Other minor fixes and improvements.
All of this can be found in the Hak5 forums.
I had no issues with the update and have had no issues so far.
Evil Portal
Now to get started I would suggest watching Chris Haralson's How to video on the captive portal, I have found his videos really helpful http://youtu.be/nw4bo4rXGgQ.
After installing the infusion from the Pineapple Bar, you will then need to install the dependencies.
Once complete you can start moving forward.
The first tab details all of the configuration changes you will need to make, the next two configure the UHTTP Deamon and NoDogSplash, the two tabs are for editing and previewing the splash.
The configuration changes made to UHTTP Deamon and NoDogSplash are also covered in the video.
UHTTP Deamon - Change "list listen_http 0.0.0.0:80" to "list listen_http 0.0.0.0:8080"
NoDogSplash - Add to "FirewallRuleSet users-to-router"
"FirewallRule akkow TCP port 8080"
After installing the infusion from the Pineapple Bar, you will then need to install the dependencies.
Once complete you can start moving forward.
The first tab details all of the configuration changes you will need to make, the next two configure the UHTTP Deamon and NoDogSplash, the two tabs are for editing and previewing the splash.
The configuration changes made to UHTTP Deamon and NoDogSplash are also covered in the video.
UHTTP Deamon - Change "list listen_http 0.0.0.0:80" to "list listen_http 0.0.0.0:8080"
NoDogSplash - Add to "FirewallRuleSet users-to-router"
"FirewallRule akkow TCP port 8080"
"FirewallRule akkow TCP port 1471"
At this point don't forget to restart the UHTTP Deamon before starting NoDogSplash.
Now this is where I have differed from Chris, Chris created a portal that worked as you would expect you preform a particular function and you get access to the web. I just prefer to mess with people, or should I say myself as doing this in the wild can be viewed as illegal. So my captive portal is just a ASCII art skull and crossbones that plays a creepy laugh with not click though.
One note to point out is you are limited by the internal storage space of the pineapple, I was unable to get the creepy laugh working but the main HTML page worked so I was happy.
Remember that this should only be done on your own equipment or equipment that you have permission to work on.
At this point don't forget to restart the UHTTP Deamon before starting NoDogSplash.
Now this is where I have differed from Chris, Chris created a portal that worked as you would expect you preform a particular function and you get access to the web. I just prefer to mess with people, or should I say myself as doing this in the wild can be viewed as illegal. So my captive portal is just a ASCII art skull and crossbones that plays a creepy laugh with not click though.
One note to point out is you are limited by the internal storage space of the pineapple, I was unable to get the creepy laugh working but the main HTML page worked so I was happy.
Remember that this should only be done on your own equipment or equipment that you have permission to work on.
Saturday, 8 March 2014
Windows 7 auto log in.
Well after spending a lot of time on WiFi Pineapples shall we head back to Windows 7.
May of you may not remember computers pre Windows XP, we never had to log in to a system, it used to just start up ready for us.
My desktop doesn't travel around, any I am the only person with access, so why should I have to type in my password to get access? Don't get me wrong my laptop does travel and as a result has a password and full drive encryption.
Now this is the same case with my mother, but I don't want her having admin access to her computer, that would only make more work for me in the long run. As this is the second time I have had to reinstall a full OS for her.
The default log in account can be a user or an admin, bear in mind if the user attempts to access and admin feature they will be prompted for the admin's password (installed team viewer for my Mum).
Less of my life and lets get into this nice quick tip.

Open the run command by pressing GUI+r.
May of you may not remember computers pre Windows XP, we never had to log in to a system, it used to just start up ready for us.
My desktop doesn't travel around, any I am the only person with access, so why should I have to type in my password to get access? Don't get me wrong my laptop does travel and as a result has a password and full drive encryption.
Now this is the same case with my mother, but I don't want her having admin access to her computer, that would only make more work for me in the long run. As this is the second time I have had to reinstall a full OS for her.
The default log in account can be a user or an admin, bear in mind if the user attempts to access and admin feature they will be prompted for the admin's password (installed team viewer for my Mum).
Less of my life and lets get into this nice quick tip.

Open the run command by pressing GUI+r.
type in "control userpasswords2" and yes without the quotes.
Then click Apply.
At this point you will be prompted for your password.
Now after the next boot you will be delivered to your desktop.
Don't forget what your password is, you may still want to lock your computer when friends come around or if you have set your computer to prompt for a password after recovering from screensaver.
So I think the next one will have to be how to reset your password if you forget it.
WiFi Pineapple SSL Strip
SSL is used for secured traffic on websites, while it was first used on banking and shopping websites, it is now used by twitter, facebook and even google.
Now the first thing you should be doing is updating to the latest WiFi Pineapple firmware version 1.1.0.
Flashing is very easy just open the WiFi Pineapple MK5 large tile and check for upgrades, flashing takes a few minutes so you may have to put some time aside for this.
Getting started is easy as with all others just click start in the small tile - you can look at the log file in the small tile but I would suggest opening up the large tile.
I attempted to access facebook I had a few problems getting the infusion to log any data, as I was using Chrome that I was logged into was forcing me to use HTTPS as but after logging out and manually typing in www.facebook.com.
I will be logging into facebook with the accoutn chump@facbook.com and the password "lamepassword"
Even though I prefer using the large tile interface, the it turns out the small tile was best for demonstrating on here.
As you can see this has reported a username and password.
You do have to pick it out but 3rd line from the bottom you can see
"&email=chump%40facebook.com"
"&pass=lamepassword"
The reason that the @ symbol is not displayed is because of Percent-encoding or URL encoding.
I won't be covering this in depth basically some characters are unsupported and need to be re-encoded. If you have ever cut and pasted a URL and accidentally included a space you would see that space replaced with %20, for further reading please see the Wikipedia page here and I also found a useful table here.
Remember to keep safe and only exploit systems you have the correct authorisation for.
After the firefox extension Firesheep received mainstream media coverage pretty much all social media sites defaulted to HTTPS / SLL, previously most of these website offered HTTPS as an option within the security settings but most users did not know how to enable this or how important it was.
Now SSL would protect you from a man in the middle attack like firesheep but SSL Strip is another MITM attack.
Flashing is very easy just open the WiFi Pineapple MK5 large tile and check for upgrades, flashing takes a few minutes so you may have to put some time aside for this.
I attempted to access facebook I had a few problems getting the infusion to log any data, as I was using Chrome that I was logged into was forcing me to use HTTPS as but after logging out and manually typing in www.facebook.com.
I will be logging into facebook with the accoutn chump@facbook.com and the password "lamepassword"
Even though I prefer using the large tile interface, the it turns out the small tile was best for demonstrating on here.
As you can see this has reported a username and password.
You do have to pick it out but 3rd line from the bottom you can see
"&email=chump%40facebook.com"
"&pass=lamepassword"
The reason that the @ symbol is not displayed is because of Percent-encoding or URL encoding.
I won't be covering this in depth basically some characters are unsupported and need to be re-encoded. If you have ever cut and pasted a URL and accidentally included a space you would see that space replaced with %20, for further reading please see the Wikipedia page here and I also found a useful table here.
Remember to keep safe and only exploit systems you have the correct authorisation for.
Wednesday, 19 February 2014
WiFi Pineapple Random Roll
 WiFi Pineapple Random Roll
WiFi Pineapple Random Roll
I'm not too sure if anyone out there is actually following this blog or not but for the 1 or 2 of you out there I have been away for a month or so after getting sick, once I got better I had lost my motivation - this has now returned.So lets stat with Random Roll, this is a Pineapple Bar Infusion, free space required is 18954kb - so you will only be able to install this on to your SD card. Random Roll installs 7 "rolls" on to your system. including Nyan cat, Peanut Butter Jelly Time and Circus Afro.

After installation you can decided to run 1 or a multiple of the rolls on a random setting, don't forget to start the service - I spent 15 minutes head scratching with this once.
Without any further configuration any user on the Pineapples network will only be rolled if the attempt to access 172.16.42.1.
After configuring DNS Spoof you will be able to direct certain websites - or if you would prefer all websites to 172.16.42.1 to roll everyone.
Now as I said in my last post if you misuse these tools you can land yourself in legal trouble, only use these tools when you have permission.
My next post will be on SSL Strip with the Pineapple and hopefully by that time I would have sorted out getting my youtube account up and running the first 2 videos will be on Karma, Random Roll and SSL Strip. Any suggestions or requests please leave a comment or PM me.
Subscribe to:
Comments (Atom)