Monday, 18 May 2015
Hacking Metaspoitable2 without Metaspoit
So been in my new job now for some time and still have not taken my Cisco courses but never mind there is nothing like procrastinating.
So Metaspoitable2 is a vulnerable by design VM that hosts numerous miss-configured" services that will allow exploitation. I downloaded my copy from sourceforge.
For the running the VM I used the latest version of VMware Player, you need to extract the files from the compressed folder, but if you are reading this that should not be a problem for you.
Right so first things first lets start with a basic nmap scan.
As you can see there are many ports running services on Metaspoitable2.
The service I am interested in is nfs running on port 2049.
Now nfs is a network file system or a network share.
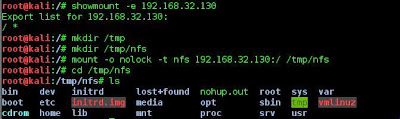
So the next plan is to check to see were in the file system the share is located and then attempt to mount it.
The showmount command gives an output of / * meaning that the root of the directory is shared. I then mounted the nfs into /tmp/nfs now we have control of the file system.
Now this took a little time to get to and now you need to looking at how the system works.
Referring back to the nmap we can see that ssh is enabled.
Now as we have access to the file system it is possible to generate an ssh key and add it to the authorized keys file.
This will allow you to ssh in to Metaspoitable2 as root without having to provide a password, going by the rules of 2 is 1, 1 is none we currently have nothing.
The reason we have nothing is because if a server admin were to update the authorize_keys file then we would loose access. So to ensure access why don't we extract the user passwords for the server.
So as the passwords are encrypted we need to unshadow the passwd and shadow files. The output is then feed into John the Ripper giving 6 usernames and passwords within 2 seconds but not the root password, I left mine running for quite some time and never got the password, however if you ssh in as msfadmin you can use the command sudo su to elevate to root.
Labels:
hacking,
IT,
John the Ripper,
Kali,
Kali Linux,
metaspoilt,
metaspoitable,
metaspoitable2,
nfs,
nmap,
root,
ssh,
sudo
Subscribe to:
Post Comments (Atom)





No comments:
Post a Comment